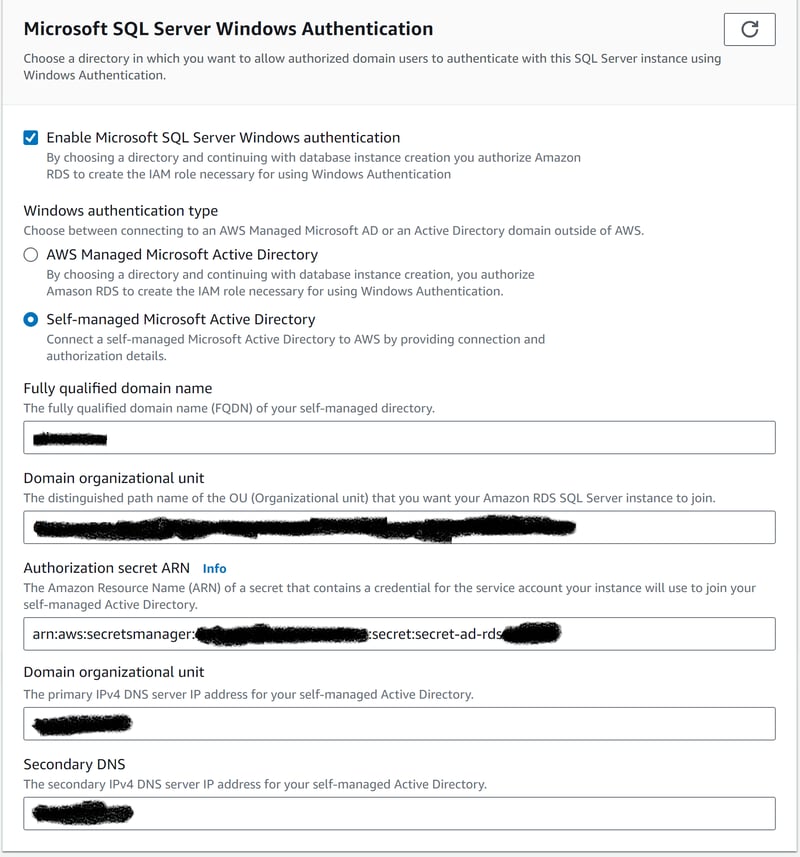
Enabling Windows Authentication seems like an easy deal, you only need to configure some info that your organization must provide you:
Fully qualified domain name. It’s often a URL like microsoft.com
Domain organization unit. It will look like this: OU=AWS_ACCOUNT_NAME,OU=A_NUMBER,DC=YOUR_ORGANIZATION
Authorization secret ARN. The Active Directory credentials (user and password).
Domain organization unit. Some range of IPs.
Secondary DNS. Another range of IPs.
However, the tricky part is to configure the secret since it’s unclear. The first part is to Store a new secret.
Then, you need to choose, Other type of secret:
You need to store the following keys:
CUSTOMER_MANAGED_ACTIVE_DIRECTORY_USERNAME: Your AD user.
CUSTOMER_MANAGED_ACTIVE_DIRECTORY_PASSWORD: Your AD password.
After you have created the secret, you must make some changes to the Resource permissions section.
Search for the Principal section and secure the RDS info is there:
“Service” : “rds.amazonaws.com”
}
After this is done, check if the Condition section exists and if not, modify it like this:
“StringEquals” : {
“aws:sourceAccount” : “YOUR_AWS_ACCOUNT_ID”
},
“ArnLike” : {
“aws:sourceArn” : “arn:aws:rds:YOUR_REGION:YOUR_AWS_ACCOUNT_ID:db:*”
}
}
Where:
The aws:sourceAccount is your AWS account ID.
The aws:sourceArn is the one that enables the RDS that can have access to your secret. In this example, I gave access to all DBs inside our AWS account by using the *.
This should be enough to enable you to access your Self Managed Active Directory.
Follow me on: