Exploring AWS !!
Day 39:
Amazon RDS — Part 2
Previously we’ve learnt about backups, read replicas and disaster recovery strategies of RDS. Today we will dive deeper into some other concepts of RDS.
RDS Security — Encryption:
Encryption at Rest-
Possibility to encrypt master and read replicas with AWS KMS-AES-256 encryption.
Encryption has to be defined at launch time.
If Master is not encrypted, Read Replicas cannot be encrypted.
Transport Data Encryption (TDE) available for Oracle and SQL server.
In Flight Encryption-
SSL certificate to encrypt data to RDS in flight.
Provide SSL options with Trust Certificates when connecting to database.
To enforce SSL-
PostgreSQL: rds:force_ssl=1 in the AWS RDS Console (Parameter Groups)
MySQL: within Database: GRANT USAGE ON . TO ‘mysqluser’@’%’ REQUIRE SSL;
RDS Encryption Operation:
Encrypting RDS Backups:
Snapshots of unencrypted RDS databases are unencrypted.
Snapshots of encrypted RDS databases are encrypted.
Can copy a snapshot into an encrypted one.
To encrypt an unencrypted RDS database:
Create a snapshot of unencrypted snapshot.
Copy snapshot and enable encryption for snap.
Restore database from encrypted snapshot.
Migrate applications to new database and delete old database.
RDS Security — Network and IAM
Network security:
RDS database are usually deployed in private subnets, not in public.
RDS security works by leveraging security groups (same concept as for EC2 instance) — it controls which security group/IP can communicate with RDS.
Access Management:
IAM policies helps control who can manage RDS (through RDS API)
Traditional username and password can be used to login to database.
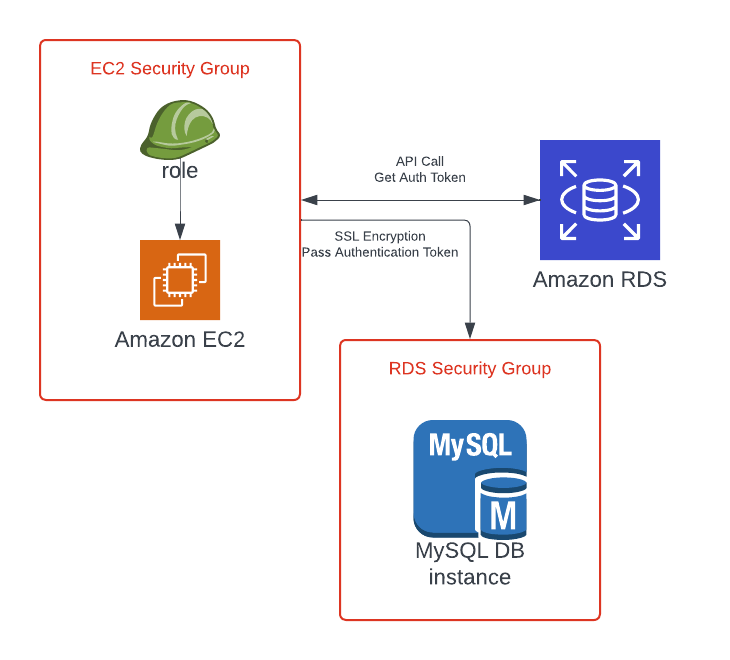
IAM based authentication can be used to login into RDS MySQL and PostgreSQL.
RDS IAM Authentication:
IAM database authentication works with MySQL and PostgreSQL.
You don’t need password, just need an authentication token through IAM and RDS API calls.
Authentication token has a lifetime of 15 mins.
Benefits:
Network in/out must be encrypted by using SSL.
IAM to centrally manage user instead of database.
Can leverage IAM roles and EC2 instance profiles for easy integration.
RDS Security Summary:
Encryption at Rest:
is done only when you first create a database instance.
or: unencrypted database -> snapshot -> copy snapshot as encrypted -> create database from snapshot.
Your Responsibility:
Check ports/IP/SG inbound rules in database’s security groups.
In-database user creation and permission or manage through IAM.
Creating database with or without public access.
Ensure parameter group or database is configured to only allow SSL connection.
AWS Responsibility:
No SSH access.
No manual OS patching
No way to audit underlying instance.